15:47, October 23rd, 2007 by david
The October edition of Elsevier’s Network Security publication contains part one of an article on web application attacks written by David Watson of the UK Honeynet Project, with the second part to follow in November.
Posted in UK News, Whitepapers | Comments Off on “Web application attacks” article published in Network Security (Part 1)
10:50, October 22nd, 2007 by david
The line-up for this years PacSec07 conference in Tokyo on November the 29th was announced today, and will include a presentation on deploying and operating a global distributed honeynet by David Watson of the UK Honeynet Project. This presentation will follow up on previous EuSec and CanSec lightning talks about GDH and will hopefully coincide with the release of more public information about the GDH research initiative.
Posted in UK presentations | Comments Off on PacSec07 schedule announced
18:47, October 14th, 2007 by david
David Watson was interviewed this week by BBC News, for piece on identity theft and attacks against Internet users.
Posted in UK News | Comments Off on BBC News “Identity Fraud” interview
10:23, October 8th, 2007 by david
The Honeynet Project published it’s annual status report today, which includes a round up the R&D activity undertaken by members during the previous year. Details of some UK Honeynet Project are also included.
Posted in News | Comments Off on Honeynet Project annual status report published
15:41, September 14th, 2007 by david
The New Zealand Honeynet Project have been busy with version two of their Capture-HPC client honeypot application, which we use internally for crawling and analysis of suspect URLs. Some of the new features include:
* support for any client application that is http protocol aware (for example, Microsoft Excel)
* ability to automatically collect malware
* ability to automatically collect network traffic on the client
* ability to push exclusion lists from the Capture Server to the Capture Client
* improved control of Internet Explorer: obtain HTML error codes; specify visitation delay after page has been retrieved; retry visitation of URLs in case of time outs or network errors)
* support for plug-in architecture, that allows to create fine grained control of clients (for example, as provided for Internet Explorer), but also allows for integration of client applications that require complex interactions to retrieve content from the web ( e.g. Safari is such an application. It doesn’t allow retrieval of web content by passing the URL as a parameter)
Highly recommended if you are interested in research in this area, as it is very actively maintained and has been effective in our experience.
Posted in Tool Releases | Comments Off on Version 2 of Capture-HPC client honeypot released
15:07, September 6th, 2007 by david
Lance Spitzner was one of the keynote speakers at Hack-In-The-Box 2007 in Malaysia this week, and talked about some of the research we have been involved in recently (including the Honeynet Project’s Global Distributed Honeynet initiative – GDH, which David led). More details can be found at the conference web site.
Posted in Events, News | Comments Off on Lance Spitzner HITB keynote
19:49, August 30th, 2007 by arthur
I’ve wanted to post this graph for a while but only just got round to anonymising the data.
Looking at piles of IRC logs can be very unilluminating, but it’s not obvious what to do with all the data. One nice way of getting a handle on links between channels is to plot channels with links between them weighted by the number of users in common.
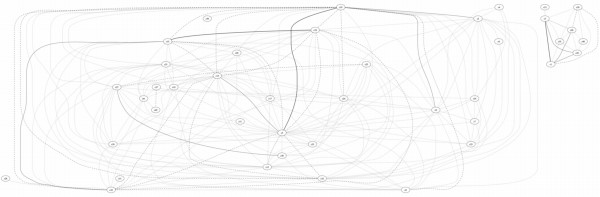
The example above is from a honeynet we ran in 2004/5. The graph shows up a couple of things nicely:
1) There are two distinct groups of channels, and a look at the data shows that there two groups correspond to channels in different languages and,
2) The strong links between a couple of channels in the main group show up that these channels are related and looking at the data shows them to be used for discussing hacking, while the other channels are innocuous.
The original channel names have been replaced by ‘cN’ to protect the guilty.
Posted in HOWTO | Comments Off on Visualising IRC data
11:53, August 30th, 2007 by arthur
There’s an interesting Google Tech Talk by Ross Anderson on ‘Searching for Evil’ about his work on looking at how “evildoers” network and the implications this has.
http://video.google.com/videoplay?docid=-1380463341028815296
Posted in Link | Comments Off on Interesting Google Tech Talk
 Welcome to the UK Honeynet Project
Welcome to the UK Honeynet Project